Free Cyber Health Checkup 🏙️ Find out how your security stacks up. Request Now >
February 15, 2022
4 Ways to Modernize Your Endpoint Experience
September 27, 2021
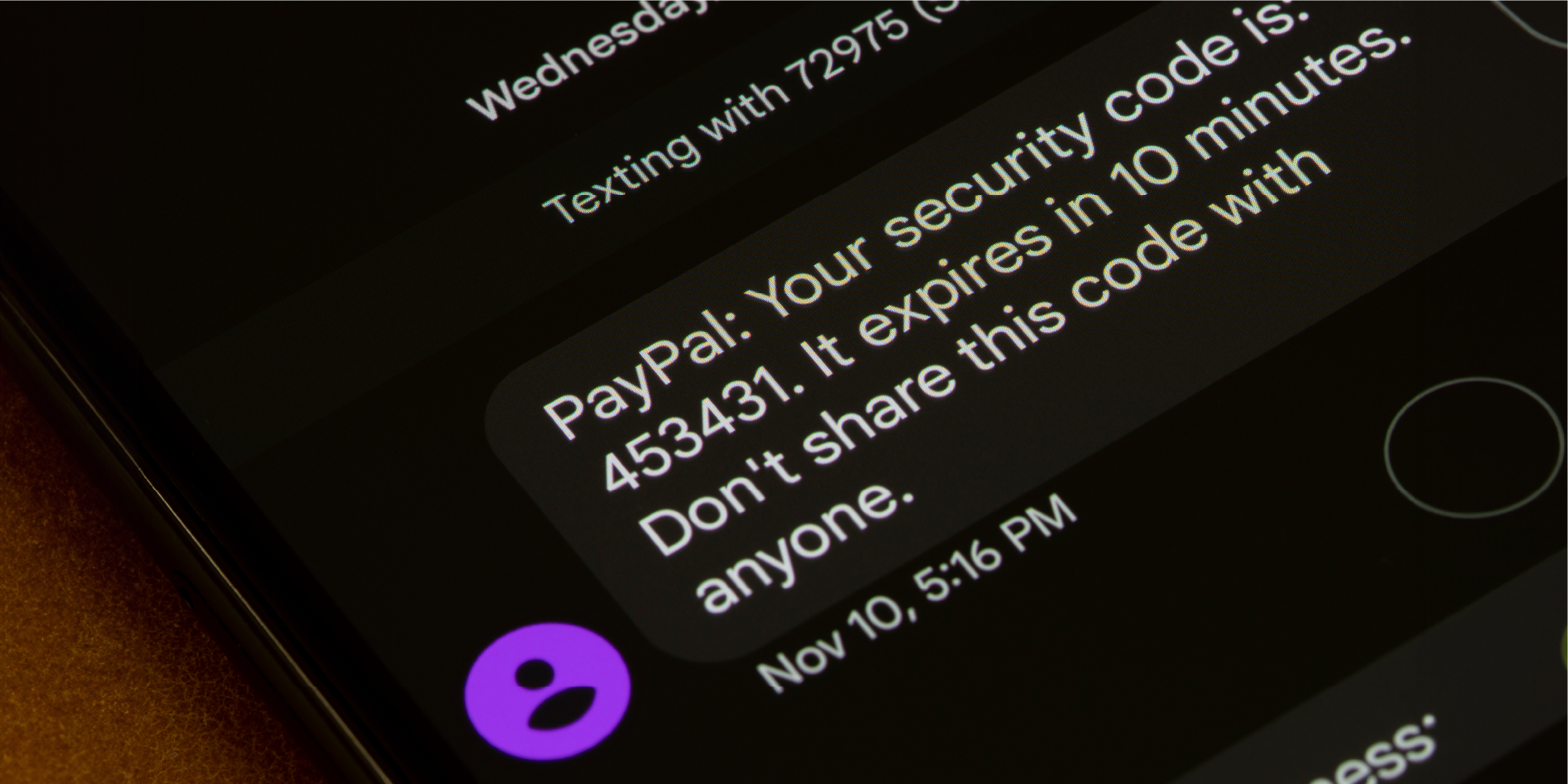
SMS Phishing: How to Avoid SMiShing Attacks
September 21, 2021
4 Reasons to Upgrade to Microsoft 365 Business Premium
September 5, 2019
The Pros and Cons of Single-Sign-On Identity Management
December 22, 2016
Cloud Computing Security Questions to Ask Providers
September 11, 2014
Lack of Due Diligence: How It Can Hurt Your Company
February 16, 2012
Planning a Virtualization Budget with IT Services

.png?width=1024&height=512&name=iCorps%20Flat%20Blue%20Transparent%20Logo%20(Black%20Lettering).png)























































































































































![[WEBINAR] Making Cyber Insurance Work for Your Business](https://blog.icorps.com/hubfs/DataStream%20Webinar%20Blog%20Image.webp)





























































![[VIDEO] How to Secure Your Network with a Zero Trust Security Model](https://blog.icorps.com/hubfs/2021%20Webp%20Image%20Files/Blog%20Images/Embracing%20a%20Zero%20Trust%20Model%20Blog%20Image%20Webp.webp)
![[WEBINAR] Why Businesses Are Choosing Microsoft Teams for Telephony](https://blog.icorps.com/hubfs/2021%20Webp%20Image%20Files/Blog%20Images/Why%20Business%20Are%20Choosing%20Teams%20for%20Telephony%20Blog%20Image%20Webp.webp)
![[WEBINAR] How to Secure Remote Workers with Microsoft 365](https://blog.icorps.com/hubfs/2020%20Web%20and%20Landing%20Pages/Content%20Images/Nauset%20Construction%20Client%20Case%20Study.png)













![[VIDEO] 3 Questions You Should Be Asking Your IT Provider](https://blog.icorps.com/hubfs/2021%20Webp%20Image%20Files/Blog%20Images/7%20Webp.webp)


![[VIDEO] 6 Ways Cloud-Based Email Can Optimize and Secure Your Inbox](https://blog.icorps.com/hubfs/2021%20Webp%20Image%20Files/Blog%20Images/6%20Ways%20Email%20can%20Optimize%20Blog%20Image%20Webp.webp)


![How to Plan a Private Data Center Migration [VIDEO]](https://blog.icorps.com/hubfs/2021%20Webp%20Image%20Files/Blog%20Images/Moving%20Exchange%20to%20the%20Cloud%20Blog%20Image%20Webp.webp)