The cyberattack landscape has heightened compliance risk for organizations. As organizations continue to implement new digital initiatives and assets, they also expand their attack surface. This is why it's critical to understand your operations and assets.
Here Are 8 Ways to Secure Your Business' Digital Assets:
1. Define Asset Categories
Digital assets are files and data that exist on a digital computer system or storage drive. These assets can be at high risk as more users access them, and are extremely desirable to cybercriminals looking to hack your system and hold your data hostage. To protect this data, you need to constantly classify your IT assets and consider implementing a managed network security strategy that centralizes and strengthens your organization’s cyber defense. Grouping assets by category can provide a high level overview of your environment and guide decision-making.

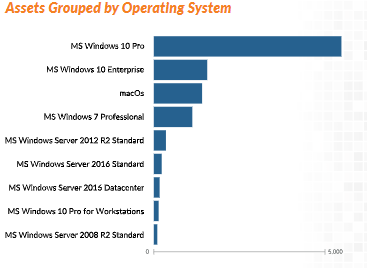
2. Take Inventory of Operating Systems
Grouping assets by their operating systems allows you to answer important questions about your business. Which employees are running an old version of Windows? Which are running on Apple versus Windows software? If you want to harden your organization's security posture, you need to be able to patch and upgrade systems as they're released. This protects your employees and sensitive data from system exploits, and can help you develop a plan to phase out older operating systems.
3. Get to Know Common Processes
Taking inventory of daily processes can help you identify redundancies that squander resources and may be susceptible to exploitation. Your IT team should be aware of the top active system processes throughout your digital environment and understand baseline activities. If an abnormality occurs, your team should be able to identify and investigate as needed.
4. Wrangle Software Installations
The first step to uncovering software vulnerabilities is to understand the dispersal of commonly installed assets across your network. This is an often overlooked concern - and one which was in the news recently when Banner ERP software left 62 colleges vulnerable to cyberattacks due to an unpatched exploit. If you have clear insight into your software installations, your team can cross-check with known vulnerabilities and exposures and prioritize updates.
5. Learn Where Your Assets are Located
If you categorize your assets by location, your IT team can assess the potential risk of certain behaviors. For example, if you have employees who travel as part of their job requirements, work from home, or check in on company devices while on vacation. An unexpected login from a new location could be flagged as an attempted hack, but may very well be an employee working on-site with a client. Without a clear understanding of how your employees work, you may cause unnecessary confusion.
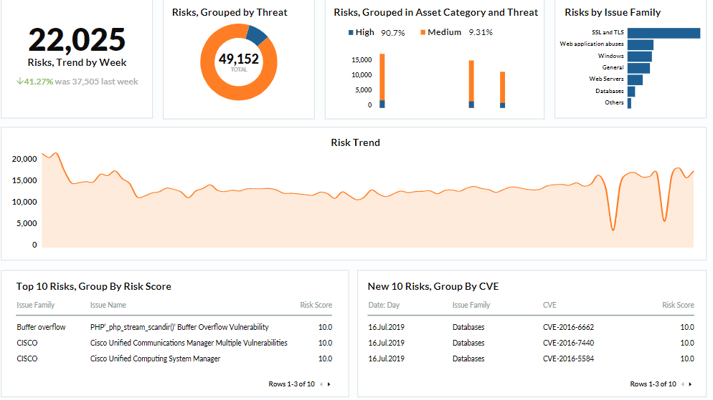
6. Understand Risk Trends
Understanding how your organization's risk posture changes each week is critical to protecting your network. New vulnerabilities emerge all the time and may require immediate action by your team. Your IT team should receive routine updates about emerging risks, common threats in your industry, software-specific exploits and patches, and risks by issue family, such as databases and web servers.
7. Personalize Your Approach to Risk
When it comes to cybersecurity, there isn't a one size fits all solution. However, there are common denominators that make securing your digital footprint much easier. For example, we recommend implementing a 24x7 network monitoring and threat detection platform, such as SOC-as-a-Service, to track network, log, and Office 365 threats. It is also worth investing in employee education, in the form of personalized cybersecurity training and phishing attack simulations.
8. Group and Prioritize Risks
Types of attacks and new threats are constantly evolving. The exploitation tactics that cybercriminals are using now, will not be the same in the future, so it's important to group new risks by family, name, and risk score to ensure that your team can tackle new challenges as they emerge. If you want to learn more about securing your digital assets, reach out to us for a free security consultation.

.webp)



