Endpoints are the most vulnerable components of your computing environment, and yet most organizations let their controls degrade. A recent study by Absolute Software found that 76% of organizations have increased their use of endpoint devices since the onset of Covid-19. To adapt to the shifting threat landscape, 82% of IT security decision makers had to re-evaluate their existing cybersecurity policies to meet this growing demand for mobility. As endpoints grow increasingly complex - whether due to bring your own device (BYOD) work environments, or internet of things (IoT) devices touching the network - risk is increasing.
Here's what Absolute Found, and Five Ways to Keep Your Endpoints Secure:
The Security Gap
For most organizations, the security triad consists of data encryption, endpoint security tools to fend off cyber threats, and client and patch management to ensure applications are free of vulnerabilities. When the world went remote, this became more complicated. Absolute found that 60% of organizations only have insight into 3/4 of their network devices. The remaining 25% is a blind spot that makes real-time incident response impossible. Absolute identified four recurring trends across organizations:
- Vulnerabilities are going unaddressed
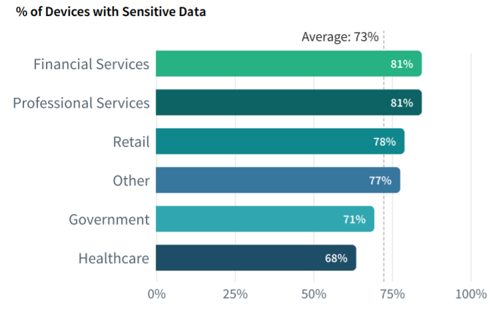
- More sensitive data on more devices than ever before
- Endpoint complexity is exacerbating risk
- Compromised end-user controls are widening the attack surface
Overall, there has been a 17% increase in the amount of sensitive data on end-user devices, year over year. On average, enterprises have an average of 96 unique applications per device. And even though much of this complexity is driven by security tools, increased complexity can become its own vulnerability.
A recent Ponemon study highlights how this complexity manifests. Participants were asked to list the security risks their are most concerned about in their organization. Their responses are presented in descending order below:
- 47% - Lack of physical security in the workspace
- 32% - Risk of a malware infection
- 24% - Criminals gaining control of a remote device to steal sensitive user/corporate data
- 23% - Securing external communications
- 20% - Securing extended business networks
Of course, the cost of implementing and maintaining endpoint security isn't the only factor driving these concerns. Sophos found that the average organization loses 41 days per year investigating non-issues. 80% struggle to perform thorough threat detection and response, often because they lack the necessary security expertise, or their internal teams are already bogged down with break-fixes. This leaves a lot of time for actual threats to go unnoticed - up to 13 hours for most businesses.
Protecting Your Employees
To combat endpoint degradation, and IT fatigue, your tech leadership needs to have a thorough understanding of what's happening on an organization-wide to device-by-device basis. This level of oversight is critical in thwarting threats, responding to suspicious events, and keeping employees secure both in and out of the office network. Here are five ways to move your company in this direction:
-
Outfit employee endpoints with anti-virus software, multi-factor authentication, and automated application updates. These simple protections will go far in securing your client data.
-
Delete unnecessary customer and employee data from endpoint devices. Routine data minimization is not only an industry best practice, it decreases the chances of accidental loss or corruption.
-
Consider implementing Microsoft's Enterprise Mobility + Security. This suite combines Azure Active Directory, Rights Management, InTune, and Threat Analytics for cost-effective, comprehensive security across devices, applications, and data. Automated behavioral analytics identify suspicious activities before they become a problem.
-
Keep your certifications and technology up to date. Ensure your company has implemented routine patches for endpoints, and that all licensing reflects the latest in compliance and regulatory standards.
-
Update your security and recovery plans to reflect the latest additions/changes to your network infrastructure. This is imperative if you have added new mobile, IoT, or on-premise resources.
If you are looking to implement changes for secure endpoints, but don't know where to begin, consider reaching out to iCorps for a free consultation.





