The FBI is warning organizations that the prevalence of Business Email Compromise (BEC)/Wire Fraud email is growing at a rapid pace. In 2020, the FBI received upwards of 19,000 BEC complaints with losses totaling $1.8 billion dollars. These scams have proliferated in recent years, driven largely by the growing cryptocurrency market. Although these scams are pernicious, there are strategies your business can employ to keep users safe online.
How to Protect Your Business from BEC Emails:
Noticing Signs of Fraud
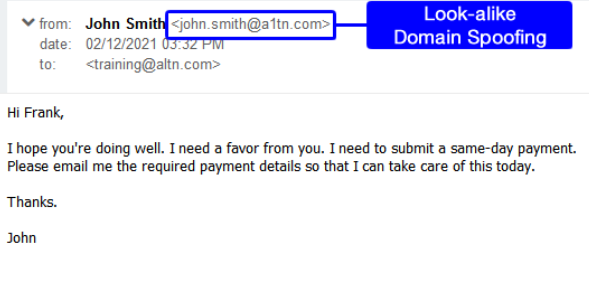
According to the FBI, BEC is most commonly known as “a sophisticated scam targeting businesses working with foreign suppliers and/or businesses that regularly perform wire transfer payments.” Cybercriminals will register a domain similar to that of the company and set it up for mail delivery, mimicking a high-priority employee such as a CEO, company attorney, or trusted vendor. The hackers research and target employees who are responsible for money handling and request a fraud wire transfer of funds. Read on to learn about the most common types of BEC scams.
1. “CEO Fraud” or “Business Executive Scam”
As seen in the video below, cybercriminals will often masquerade as high-level executives or other legal representatives. This strategy targets employees in charge of finances, most often accountants, Directors of Accounting, and CFOs. Posing as the C-level executive, the cybercriminal will reach out to the financial employee to request a wire transfer, sending the funds directly into an account controlled by the cybercriminal. Some common reasons given for needing the transfer include the C-level employee being stuck somewhere with legal issues or having an urgent bill that needs to be paid; these scenarios stimulate a sense of urgency, taking advantage of the human response and making the scam easier to execute.
2. “The Bogus Invoice” or ”Invoice Modification Scheme”
A bogus invoice will usually involve a business that has an established relationship with a particular supplier or client. Cybercriminals will compromise an employee's email address to gain access to the business account. This account is then used to send false notifications to customers asking for an invoice payment, and the money transfer is sent into a fake account benefiting the criminal.
3. “Compromised Employee Account”
Cybercriminals will often go directly to the employees of any organization, hacking right into their email accounts to request payment. This payment is sent directly to a criminal-controlled account. These messages are usually sent to multiple vendors but are not mass-emailed in order to avoid being marked as spam. Businesses are usually not aware this scam has occurred until their vendors follow up to check for an invoice payment status. Scam victims are varied, ranging from small local businesses to large-scale corporations. Unlike general phishing scams, attackers will spend significant time doing their research on the intended victim to ensure that the message sounds believable and legitimate.
4. Spelling Errors and Malicious Attachments
Misspelled words and incorrect use of grammar are some of the most common ways to detect an email scam. Most emails that are sent within an organization have automatic spell check software, so it is unlikely that there would be multiple syntactic and grammatical errors. The more spelling errors, the more cautious you should be of an email. The same logic can often apply to attachments. Not only are misspelled attachments a red flag, but most organizations use collaboration tools such as SharePoint or Teams, often eliminating the need for email-based attachments. If you receive a suspicious email, never click on or download the attachments.
5. The "Too Good to Be True" Email
These emails are designed to get people to click, before thinking everything through. They may incentivize recipients with awards or limited-time sweepstakes, but are likely just malware conduits. Even if the sender is a familiar contact, awards without context do not bode well for your account's integrity. If you know the sender, reach out to them to verify what you've received.
Recent BEC Attacks in the News
- Toyota - Attackers managed to convince someone with financial authority to change the passwords, which ended up costing the company $37 million. This attack was relatively simple, but ended up costing the organization in financial, legal, and reputational terms.
- Acer - This was one of the largest attacks in 2021, costing the business $50 million. The cyberhackers breached the organization's system and stole 60GB of data. When the attack was recognized, Acer immediately began implementing its cybersecurity protocol. The attackers demanded $50 million.
- Puerto Rican Government - In 2020, Puerto Rico's government lost over $2.6 million in a BEC attack targeting the Industrial Development Company. The organization transferred money into a fraudulent account after receiving a demanding email. Once the government recognized what happened, they immediately called the FBI.
- Treasure Island - This homeless charity suffered a month-long BEC attack, which led to the loss of $625,000. The cybercriminals got into the system by manipulating an invoice used by one of the charity's partner organizations. The organization didn't have cyber insurance and ended up having to deal with the loss alone.
How Can You Protect Your Business?
-
Ensure that the “Reply-To” email address matches the sender's email address, but even if it does, be cautious of email-only wire transfer requests - verify any of these types of requests with the contact by phone or in person.
-
Implement multifactor authentication which requires more than one method of authentication to verify the user's identity to log in.
-
Educate and train employees on best practices - humans are busy and fallible creatures, so it's important for them to be on the lookout and recognize these types of scams before it's too late. Education is critical.
-
Partner with a Managed IT Services Provider that has expertise in security best practices and implementing the tools that make the most sense for your business.
- Use a two-factor authentication tool that requires an additional set of login information from employees. These codes change frequently and make it more difficult for hackers to gain access to your information.
- Anti-spam solutions guard against more sophisticated types of phishing such as spear-phishing and whaling. These solutions recognize false emails containing strange attachments but may have difficulties detecting emails from a compromised account.
iCorps partners with Mimecast’s security, archiving and continuity cloud services to protect business email and deliver comprehensive email risk management in one fully integrated subscription service. By reducing the risk, complexity, and cost traditionally associated with protecting email, you no longer have to manage an array of disjointed point solutions from multiple vendors. Reach out for a free consultation today.





