Despite growing awareness of phishing attacks and ransomware - no doubt due to well publicized hacks - email remains one of your company's largest vulnerabilities. Attacks feature highly personalized content, with credentials that are often scraped from real people or well known brands. But it's not just these external threats that are wreaking havoc. In 2019, 71% of organizations experienced a cyberattack due to a compromised employee account. This is why your IT team needs an end-to-end strategy in place for email threats.
Here Are Three Ways iCorps Safeguards Our Clients’ Email, and How to Tell If Your Current MSP Is Dropping the Ball on Inbox Security:
1. A Layered Approach to Platform Security
Many of our clients are leveraging cloud and on-premise services through Office 365. While Microsoft provides security tools for their applications, they require oversight for proper implementation and maintenance. Moreover, these tools only provide one layer of security - contrary to industry best practice. You should aim for a security environment with a diverse range of protections, and providers, so there is never a single point of failure. This makes your infrastructure more redundant in the event of a security incident, or unexpected downtime. For our clients, we layer Microsoft email tools such as Enterprise Mobility + Security with those from Mimecast, a third party vendor that specializes in cloud-based email security.
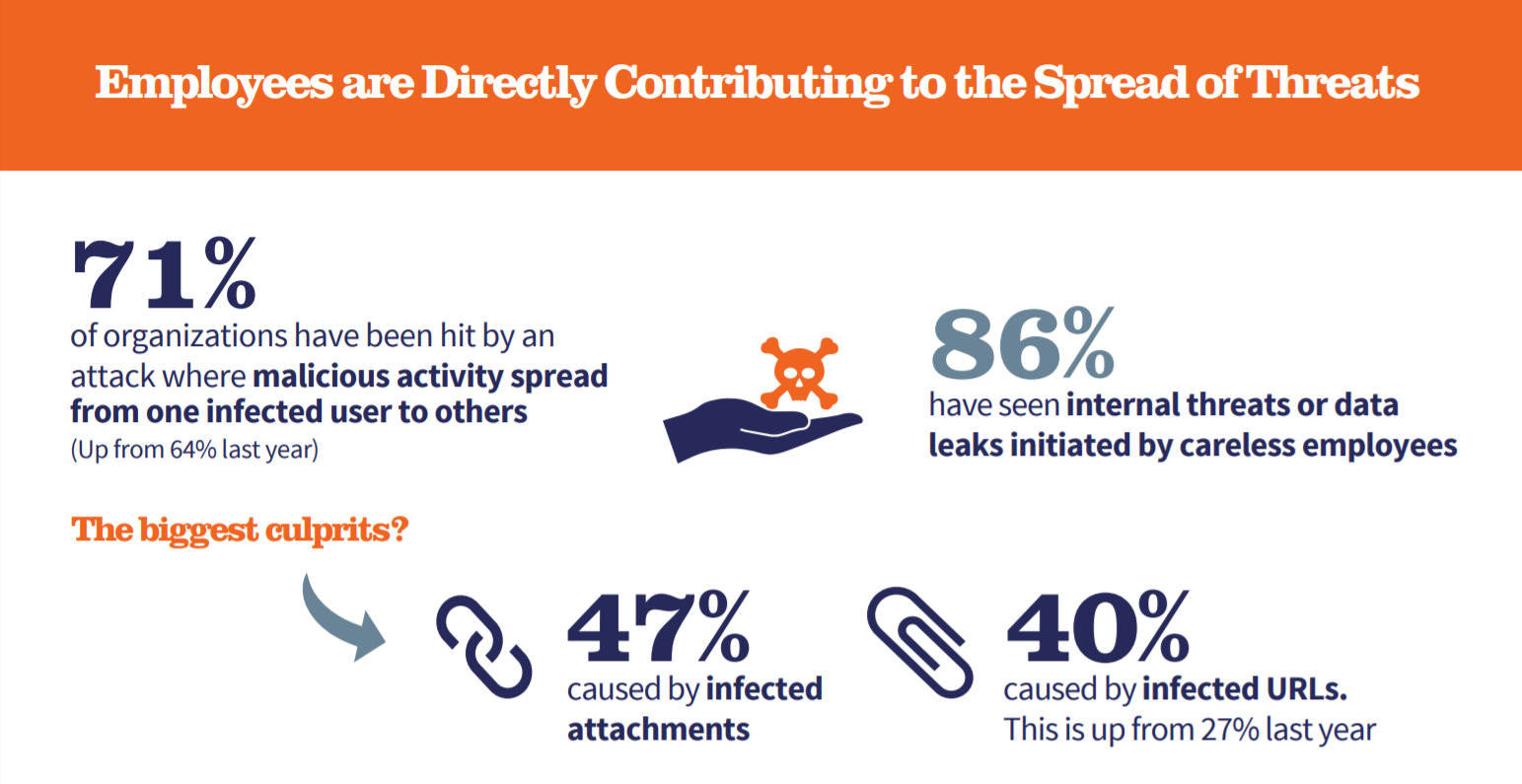 Image courtesy of Mimecast.
Image courtesy of Mimecast.
2. The Top Three Email Threats for Your Employees
When vetting our email solutions, we look for safeguards at the network perimeter, interior, and email perimeter. Mimecast offers protection in all three areas, and specializes in suppressing:
-
Ransomware: malware that encrypts a victim's information or device, until specific terms are met. Mimecast provides web security to prevent attacks from completing.
-
Spear-Phishing: campaigns that harvest user credentials via malicious site links. They are often highly personalized, are imitating a well known brand, or convey urgency to prompt user response.
-
Internal threats: originate with a compromised email account, malicious employee, or unintentional human error. Mimecast blocks email-based outbound connections to deter these threats.
With Mimecast, we establish custom security controls based on our clients' employee activity, location, correspondence patterns, etc. Once more, this mirrors strategies we leverage within Office 365, such as identity management and usage-based access controls, to keep employees safe.
 Image courtesy of Mimecast.
Image courtesy of Mimecast.
3. Proactive Email Security Saves Time and Money
Among Office 365 users who added Mimecast, 93% noticed improved defense against SPAM and email borne threats, while 89% noticed a decrease in business email compromise. IT teams were also able to save an average of 9 hours per month after implementing internal email protection. By reducing SPAM, dangerous file types, malicious attachments, and impersonation attacks, our consultants are free to pursue other security projects for our clients - without sacrificing end-user safety. Beyond threat detection, our clients leverage many of Mimecast's other tools, including:
-
Cloud Archive: systematically collects email content for streamlined management, availability, and retrieval
-
Email Backup and Recovery: provides syncing and recovery for Exchange
-
e-Discovery and Compliance: offers specialized tools to meet regulatory requirements, such as GDPR
If you're looking to implement email security and productivity tools, make sure you have the right IT team for the job. Reach out to our consultants today, for a free business IT consultation.





