Malware, or malicious software, has always existed in tandem with technological advancement. As computers and mobile devices get smarter, so too do the threats that plague them. 2017 was another banner year for cyber threats, from the WannaCry ransomware attack in May to NotPetya in June, and the Equifax, Yahoo, and Uber data breaches throughout the fall. These headlines reinforced the unequivocal need for improved cybersecurity, in a threat landscape that is constantly evolving.
How MalewareBytes are Changing
Which types affect consumers, and which target businesses?
MalwareBytes, an internet security firm specializing in disinfection and protection solutions and a Gartner "Visionary" in Endpoint Protection Platforms, may offer some insight. In their "Cybercrime Tactics and Techniques: 2017 State of Malware," MalwareBytes researchers tracked the progression of cyber threats throughout the year. Looking at detection rates for both businesses and individuals, the report provides a compelling macro-view of 2017, while forecasting emergent threats in 2018. These were the most eye-opening things we read:
Before diving into specific high-impact types, it is worth considering overall malware trends from the past two years. MalwareBytes groups these threats by target: businesses and consumers. Looking first at businesses, these shifting threats reveal much about malware success rates, and hackers' adaptation.
Top 10 Business Threats
2016 2017
| 1. Fraud tool | 1. Hijacker |
| 2. Adware | 2. Adware |
| 3. Hijacker | 3. Riskware tool |
| 4. Riskware tool | 4. Backdoor |
| 5. Backdoor | 5. Ransomware |
| 6. Hack tool | 6. Spyware |
| 7. Worm | 7. Worm |
| 8. Crack tool | 8. Hack tool |
| 9. Banking Trojan | 9. Fraud tool |
| 10. Ransomware | 10. Banking Trojan |
When comparing years, the most notable shift is the increased prevalence of ransomware in 2017. Moving from the 10th to 5th most detected threat, ransomware attacks increased by 90% for business customers. MalwareBytes attributes this to ransomware families such as WannaCry, Locky, Cerber, and GlobeImposter. They found:
- The monthly rate for ransomware attacks was 10 times higher than in 2016.
- Roughly 7% of attacks in September 2017 involved ransomware. By comparison, only 1.11% involved ransomware in 2016.
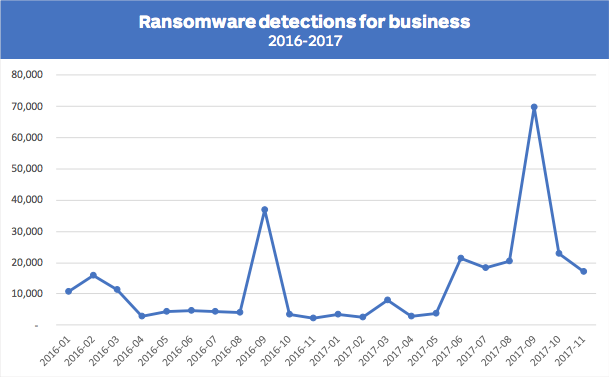 Image courtesy of MalwareBytes.
Image courtesy of MalwareBytes.
There were also increased rates of banking Trojans, spyware, and hijackers targeting companies. Unlike traditional ransom demands, these types of malware harvest "data, login credentials, contact lists, credit card data, distribute more malware, and spy on a victim for information about the business, to dig deeper into the network."
Of course, consumers also bore the cyberthreat brunt. Here are the top ten detected threats for 2016 and 2017.
Top 10 Consumer Threats
2016 2017
| 1. Fraud tool | 1. Adware |
| 2. Adware | 2. Fraud tool |
| 3. Riskware tool | 3. Riskware tool |
| 4. Backdoor | 4. Backdoor |
| 5. Hack tool | 5. Hack tool |
| 6. Hijacker | 6. Worm |
| 7. Crack tool | 7. Hijacker |
| 8. Worm | 8. Crack tool |
| 9. Banking Trojan | 9. Ransomware |
| 10. Rootkit | 10. Spyware |
MalwareBytes reported that "overall threat detections for consumers rose 12%" in 2017. Ransomware eked out a place in the top ten, with detection rates up 93% over 2016. However, it is adware that has emerged as the most persistent threat to consumers. As per the report:
- Adware accounts for 40% of consumer threat detections.
- This reflects a 132% increase over last year, when adware represented less than 20%.
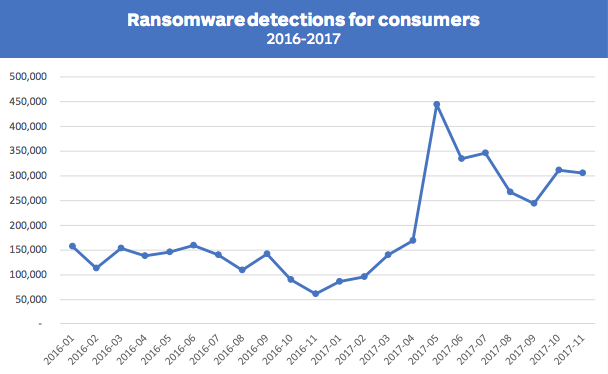 Image courtesy of MalwareBytes.
Image courtesy of MalwareBytes.
There has been an overall shift away from locked browsers, towards phishing emails and malvertising, which would account for the upswing in adware. MalwareBytes noted that "there's been a lot of clickers and bundled adware getting into the Google Play Store." Both Google and Apple stores have reported an increase in adware and malicious apps. Malvertising is particularly effective, as there is "difficulty in reproducing the attack for analysis."
Ransomware
In 2017, ransomware monopolized summer news headlines. WannaCry detections surged 375% percent from August to September. Between July and September, there was a 700% increase in overall ransomware detection.
That said, MalwareBytes found fewer types of ransomware at play, noting the "development of new ransomware families grew stale." The majority of attacks were perpetrated by a select few ransomware families, which hold the market share. These families have either crushed darknet competition with the quality of their product or have cultivated "a special relationship with the holders and herders of malicious spam botnets and exploit kits", the primary means of distribution.
In light of many high-profile ransomware attacks, there has also been greater adoption of anti-ransomware technology. As companies and consumers increase backup precautions, while implementing threat and protection standards, MalwareBytes reported "fewer cases where the ransom is paid." And cybercriminals have taken notice. In light of pro-active security, "it is more economical for criminals to utilize crypto-miners, ad fraud malware, and good old-fashioned credential stealing ransomware", all of which have seen a boom in 2017.
On the rise
-
Crypto-mining
With the proliferation of crypto-currencies, such as BitCoin and Ethereum, there has been a considerable increase in malicious attacks using crypto-miners. Cryptocurrencies run on blockchains, essentially public ledgers that have been shared and duplicated across a network of computers. These blockchains are run by miners, who receive payment for tallying ledger transactions. The process eliminates the need for an intermediary financial institution and keeps user identities private.

Image courtesy of Blockgeeks.
Crypto-mining becomes malicious when it involves "any method that uses the system resources of an unsuspecting victim in order to mine." MalwareBytes has noticed an increase in attacks using crypto-miners, as well as a diversifying attack approach. New methods include:
-
- Adware bundlers pushing miners instead of toolbars
- Compromised websites serving drive-by mining code
- Miners delivered through malicious spam and exploit kit drops
The range of mining tools is only expected to grow throughout 2018. MalwareBytes predicts the inclusion of new mining platforms "such as android and IoT devices, and new forms of malware designed to steal cryptocurrency."
-
Adware / Ad Fraud
Adware has continued to hold its spot in the top two threats for both consumers and businesses. Adware generates revenue by inundating a user with ads, redirecting search requests to websites, and collecting user data. Often one of the most visible forms of malware, this threat has continued to evolve, with hidden adware gaining traction in mobile devices. This type deceptively runs ads to collect revenue, proving a nuisance to consumers, and a waste to businesses who see their ad spending wasted on botnets that mimic real users.
This also correlates to the uptick in hijacking detections. MalwareBytes reported a 40% increase in hijackers, with attacks focused on businesses rather than consumers. As per their definition "Hijacker malware interacts and modifies victim browser operations to push advertisements, redirecting the browser to third-party search engines or shopping site." From there, the hijacker may install additional malware, or steal sensitive personal information.
In response, companies have been more aggressive about ad-blocking. Google, Mozilla, and Microsoft all support varied blocking tools on their respective browsers. However, the costs associated with "meaningful security in ad vetting and sales" still prove a hurdle to the elimination of malvertising. MalwareBytes predicts that malvertising and adware will continue to pose a considerable threat in 2018.
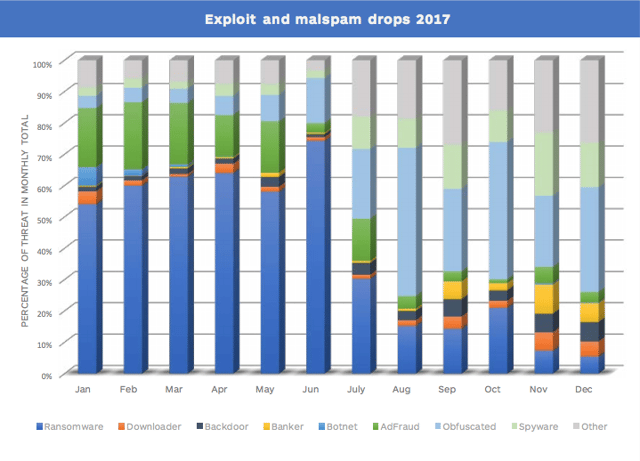 Image courtesy of MalwareBytes.
Image courtesy of MalwareBytes.
-
Spyware & Trojans
MalwareBytes reported a 30% increase in spyware detections, for 2017. Spyware is a category of malware that spies on users to collect sensitive information. This can be done by capturing data through screenshots, webcam captures, keylogging, or stealing form data from visited websites. Although spyware had a slow start to the year, it made a significant impact on "businesses and consumers during the last half of 2017." MalwareBytes attributes this to the decreased success of ransomware attacks, prompting cybercriminals to broaden their approach.
This increase also parallels a boom in banking Trojan detections. In previous years, banking Trojans had been something of a slow-growing threat. However, there was an average 102% increase in detections in the second half of 2017. MalwareBytes suggests that "the same campaign that was pushing the spyware was also pushing the banking Trojans." They concluded with the expectation to see "a continued steady stream of spyware for consumers and more big spikes against businesses in 2018".
On the decline
- Exploit Kits
Trends in cyberthreats have seen an overall shift towards social-engineering-based attacks. Social engineering works by manipulating people into volunteering confidential information, whether it be personal, or business related. Historically, this form of manipulation has proven easier than finding ways to hack software. As such, there has been a decline in the detection of exploit kits. These kits run on web servers and are particularly adept at pinpointing software vulnerabilities. MalwareBytes also attributes their decline to "the browser market share and the development of (or lack of) web exploits". Those that were active in 2017 were found predominantly in malvertising chains. From a macro-perspective, exploit kits simply aren't providing hackers the same degree of mass-scale efficiency.
- DDoS
Like exploit kits, botnet malware has also tracked a steady decline in 2017. Botnets are networks of infected computers that launch distributed denial of service (DDoS) attacks, steal data, spread malicious emails, and install further malware. Although this decrease is a good thing, MalwareBytes suggests that is "likely due to a shift in focus away from the desktop, aiming at IoT devices such as routers or smart appliances instead." These devices, which often lack regular security updates and system patches, are inherently more vulnerable to cybercriminals. It is likely that 2018 will see an increase in IoT threats, featuring crypto-mining, spam-spreading botnets, and DDoS attacks. Criminals could also pursue ransoms by encrypting devices, rather than files, until some condition has been met.
Staying safe
The most successful businesses recognize that proactivity and longevity go hand in hand. In today's world, there is no substitute for a well thought out, customized cybersecurity posture. Don't let the growing threat of cybercrime distract from your company's goals, profits, and prospects. For assistance developing, or implementing, tailored security plans, contact an iCorps expert.





